
Digital Transformation Playbook
Is your business ready to reimagine how it operates?
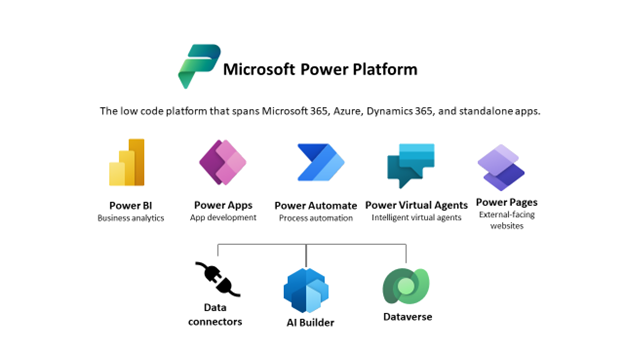
Download the EbookBy now, most customers are familiar with Microsoft Power Platform, Microsoft’s business suite of applications that enables individuals who don’t have coding experience and in-depth software programming skills to build apps, flows, automate processes and even create external-facing websites.
Power Platform consists of now five different tools — Power BI, Power Apps, Power Automate, Power Virtual Agents, and, as of June 2022, Power Pages (formally power app portals) — which together grant users the ability to generate reports, build and automate apps, build chatbots, and create user-friendly websites in-house.
Today, users of these tools have access to more than 750 connectors (and growing!), and Dataverse to create a business-focused definition of your organization’s data for use within Microsoft 365, Azure, Dynamics 365 environments, and many other services. Applications built with the Power Platform can also connect to any custom-built data connectors. With AI Builder, which is easy to connect, developers can simplify management and governance, and harness the ability to extend their apps by using built-in Azure API connectors.
With such wide-ranging access comes certain challenges, especially when it comes to best practices, guidance, and governance. Although the main appeal of Power Platform is that it democratizes programming for a new generation of citizen developers, users can potentially gain access to sensitive data. Therefore, it’s imperative for organizations that use Power Platform to implement a strong data governance strategy, to ensure data security, and that these tools are being used appropriately and responsibly.
Keep reading to discover key best practices for formulating a fool-proof Power Platform data governance strategy. But first, it’s important to know your tenant and environment.
Understanding Tenants and Environments
A tenant refers to the container in which all your different environments sit; each of these environments also acts as a container for any apps or flows you build in Power Apps, as well as for your Dataverse resources. You can have as many domains as you want within your tenant, provided you have sufficient storage space. For Dynamics 365 users, this concept is much like the development, sandbox, and production environments, each of which is a different Dataverse environment.
Data connectors and controls exist within each database environment inside the tenant. All these assets need to be secured with roles and permissions to ensure users have access only to the tools and environments they need and are restricted from the ones they do not.
Environments can be used to target different audiences and/or for different purposes. For Power Apps and Power Automate, each tenant includes a default environment where all licensed Power Apps and Power Automate users can create apps and flows. Non-default environments can be created to provide more control around permissions and can be restricted to service administrators using the Power Platform Admin Center.
With all this in mind, let’s look at our six best practices:
1. Establish a team structure for your environments.
This is an important first step before you build out your Power Platform environment. If you work in a large organization, assign your administrators the Power Platform service admin role, which will grant them full access to Power Apps, Power Automate, and Power BI, and restrict the creation of new trial and production environments to only those administrators.
Next, designate the default environment as a “personal productivity” environment for your business groups. Users can use this environment to build simple apps and flows to test Power Platform’s capabilities without connecting to Dataverse or customer data. Be sure to give this default environment a distinctive name, so that users don’t mistake it for a non-default environment.
Any mission-critical applications should be built in a non-default environment but, in the interest of security, it’s vital that you establish a policy for requesting access to or the ability to create non-default environments. To that end, it’s best to restrict non-default environment privileges to specific business groups.
2. Set up data loss prevention policies.
Data Loss Prevention (DLP) policies are designed to enforce which of Microsoft’s 800+ connectors are allowed to access important business data. These connectors fall into one of three categories: Business Data Only (BDO) or No Business Data (NBD) allowed or blocked. BDO connectors have access to important client data and are used by trusted apps. To protect that client data, connectors in the BDO group can be used only with other BDO connectors in the same app or flow. If you don’t want makers to use a specific connector, you can block it.
Tenant admins can define and design policies in such a way that they apply to all environments within your tenant, specific environments within your tenant, all environments within your tenant except one, and so on. For example, if you want to allow makers to use Microsoft connectors for business purposes, you can create a policy that spans all environments and classifies all Microsoft connectors as “Business Data.”
Once you’ve established a team structure for your environment and set up DLP policies, the next step is to start monitoring activity across your tenant.
3. Leverage out-of-the-box activity logs and analytics.
It’s important to monitor who is using your power apps and flows and how they’re using them, both to understand user adoption and to ensure security policies are effective. You can use the Office 365 Security & Compliance Center to access full logs and audit records for Power Apps and Power Automate. These logs and records will provide you with a full account of users, activities, and timelines:
| Power Apps | Power Automate |
| Created app Edited/saved app (draft) Published app Deleted app Restored an app from an app version Launched app Marked app as featured Marked app as hero Edited app permissions Deleted app permissions | Created flow Edited flow Deleted flow Edited permissions Deleted permissions Started a paid trial Renewed a paid trial |
To access logs and audit records, you must have an Office 365 E3 license or greater and have enabled security and compliance audits at an organization level.
Office 365 also enables you to use an application programming interface (API) to query this data. If you use a third-party monitoring tool, you can use this API to access activity log data for reporting purposes.
With logging out of the way, the next area on which to focus is analytics. If you currently use Dynamics 365 with Dataverse, the Power Platform Admin center offers full logs around API calls and performance within your Dataverse environment. By logging into the Power Platform Admin Center and navigating to the Analytics tab, you can track:
- Common Data Services: Who is using the system, and which tables and entities they’re using.
- Power Automate: The number of flow runs over a maximum period of 28 days as well as usage statistics for the various flows. You can also see when certain flows were created, how many flows are in each environment within your tenant, and so on.
- Power Apps: How many times apps have been launched over a maximum period of 28 days, user location, app version, and so on.
4. Build a Center of Excellence.
Rather than start from scratch, consider downloading the Power Platform Center of Excellence (CoE) Starter Kit, which is a “collection of templatized best practices” designed with administration and governance in mind. This starter kit includes the following components:
| Scenario | Toolkit Component |
| Catalog tenant resources |
|
| DLP Strategy + Visibility |
|
| Change App Ownership |
|
| Sample Audit Process |
|
| Archive unused apps |
|
| Act based on certain connector usage |
|
| Onboard new makers, provide training, and share best practices |
|
| Encourage Adoption |
|
With a clear picture of the apps within your environments, and DLP policies to ensure governance, the next step is to use that knowledge to act.
5. Establish and automate your audit process
One of the amazing things about Power Automate is that you can use it to automate your audit and alert process. In Power Automate, you can create your own workflows using management connectors that either permit or restrict behavior based on your organization’s DLP policies. For example, you could use Power Automate to create an attestation process for assets in the default environment. There are several free audit workflow templates that you can use, courtesy of Microsoft, including the audit workflow in the Power Platform CoE Starter Kit.
Consider using PowerShell cmdlets when automating your audit process. Not only will these cmdlets give you full visibility into all activity in Power Apps and Power Automate, but you can also use them to pull in the metadata you need to build reports and alerts. Best of all, cmdlets are flexible, so you can build policies you need to meet administrative and governance requirements.
6. Welcome new makers and identify champions.
Whenever you detect a new flow, check to see whether that maker is part of the makers Active Directory group. If they aren’t, that means they’re a new maker, and you should send them a welcome email that lists the company and public resources. You should also invite them to join your organization’s internal Yammer or Teams Club to share best practices. You can find a complimentary welcome email template in the Power Platform CoE Starter Kit.
In addition to welcoming new makers, you’ll also want to identify Power Platform champions who can help empower new users within your existing user base. When identifying champions, look for individuals who:
- Are diligent in their work
- Understand your company’s vision for data governance
- Demonstrate interest in the Power Platform
- Have a positive attitude
- Are well-regarded by other users
- Possess leadership qualities
When it comes to choosing Power Platform champions, keep in mind that people skills and managerial knowledge are just as important technical expertise.
—
About Hitachi Solutions
Hitachi Solutions is a global systems integrator with leading capabilities in Microsoft applications and technologies. Through advisory services, industry, and technology expertise, as well as implementation excellence, our skilled professionals support and accelerate our customers’ data and business system initiatives.
Thanks to our strong relationship with the Microsoft product team, and the depth and breadth of our Power Platform expertise, we are uniquely positioned to help customers connect technologies across the entire business enterprise and unleash the full potential of the Power Platform.
- Check out our Governance QuickStart
- Connect with us today!


